How to Make Secure Website in Wordpress
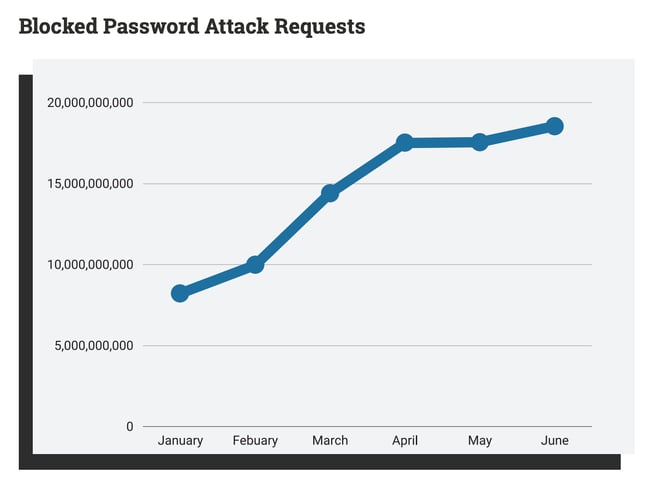
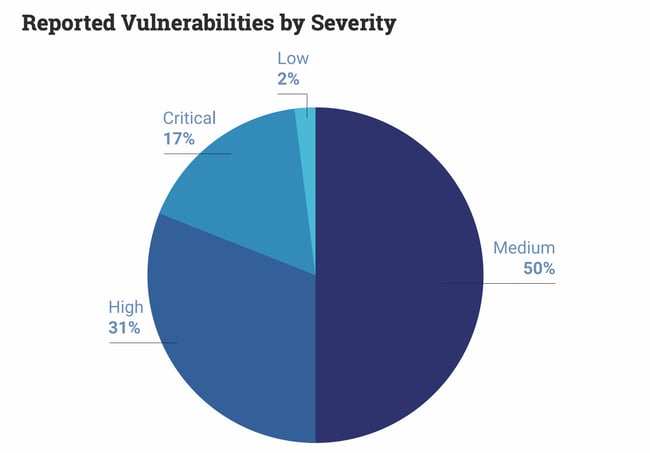
If you have an online presence, you demand to prioritize security. And if WordPress is your CMS, y'all definitely demand to prioritize security. Overall, WordPress is a secure CMS, merely considering it's open up-source, information technology suffers from various critical vulnerabilities. Thankfully, achieving WordPress security is simple when you take the correct steps. In this article, we'll become into the details of the well-nigh common and dangerous security vulnerabilities that come up with using WordPress. Then, nosotros'll cover all the steps you'll need to manage a safe, secure WordPress website. Let's hash out the reasons why every successful website congenital with WordPress prioritizes security. These apply to businesses of all sizes, reputations, and industries. If attackers attain personal information about you or your website visitors, there's no end to what they could do with the information. Security breaches open you up to public data leaks, identity theft, ransomware, servers crashing, and the list unfortunately goes on. Needless to say, any of these events is far from platonic for the growth and reputation of your business, and are usually a major waste of time, coin, and free energy. As your business organisation grows, the number of issues you'll need to solve and your customers' expectations for how you accost those bug will increase. I of those bug is keeping your customers' data secure. If you can't provide this central service from the get-get, yous volition undermine your customer's trust in you. Your customers demand to trust that their information will be used and stored safely, whether it be contact information, payment information (which requires PCI compliance), or a basic response to a survey. In that location's a catch-22 here: If your security measures work, your customers will never demand to know. If they ever do see news nearly your site'southward security, chances are it's bad news and most won't come back. Keeping your WordPress website secure is a cornerstone of maintaining a high-ranking website. Why? Because a safe website is a searchable 1. Website security directly affects visibility from a search on Google (and other search engines), and has for a while. Security is ane of the easiest ways to heave your search rank. You can read about what other factors affect how Google ranks your website in our Ultimate Guide to Google Ranking Factors. Clearly, protecting your online backdrop should be a key business. Every website needs to ensure condom for their visitors and users, and we'll go over the steps to practise this. But first, you might be wondering: Is WordPress secure? Let'due south have a look below. WordPress is a condom content direction organisation. However, it tin exist vulnerable to attacks — just like any CMS. There'due south no style around it: Websites that apply WordPress are a popular target for cyberattacks. In its WordPress security report, a firewall service named Wordfence blocked a whooping xviii.5 billion password attack requests on WordPress websites. That's nearly 20 billion attacks on WordPress websites alone. This might be less surprising, knowing that 42.7% of all websites use WordPress. Yet, well-nigh 20 billion attacks is still quite high, even when taking into account WordPress' market share. The bad news go along: 8 out of ten of WordPress security risks fall into the "Medium" or "High" severity score according to the Mutual Vulnerability Scoring System. Only before you lot difficult-delete your WordPress account, you should know that these numbers aren't entirely WordPress' fault. Or, at to the lowest degree, non the error of the WordPress product itself. WordPress employs a large security team of world-form researchers and engineers looking for vulnerabilities in its system, and regularly releases security updates to their software. As far every bit WordPress core goes, we're covered. The problem lies with how WordPress is made available to its users. WordPress is open-source software, pregnant that the source code is available for anyone to alter and distribute. Considering WordPress is open-source, the software is infinitely customizable and optimizable. There are thousands of plugins, themes, and developers with the skills to change the backend code themselves. This flexibility is a defining feature of WordPress, and a huge part of what makes it so powerful and widely-used. The downside to all this freedom is that an improperly configured or maintained WordPress website is prone to a myriad of security issues. WordPress gives a lot of power to its users, and with great power comes great responsibleness. Responsibleness that many are shrugging off. Hackers know this and target WordPress websites appropriately. Y'all can rest easy knowing the following, though: Perfect security simply doesn't be, especially online. Every bit WordPress states: "[S]ecurity...is hazard reduction, non risk emptying. It'southward nearly employing all the appropriate controls available to you, within reason, that allow you to improve your overall posture reducing the odds of making yourself a target, subsequently getting hacked." You can never guarantee consummate immunity to online threats, just you tin can take steps to make them much less likely to occur. The fact that you lot're reading this ways you probably intendance most security and are willing to get the extra mile to keep you and your visitors condom. To sum all this upward, WordPress is secure, merely only if its users take security seriously and follow best practices. So, what could happen if one chooses to push button all these numbers aside and exercise nothing to secure their WordPress site? Equally it turns out, a lot. The about mutual types of cyberattacks on WordPress websites are: This is i of the simplest types of attacks. A animal-force login occurs when attackers apply automation to enter many username-password combinations very quickly, somewhen guessing the correct credentials. Animate being-strength hacking tin can admission any password-protected information, non only logins. XSS occurs when an attacker "injects" malicious code into the backend of the target website to extract information and wreak havoc on the site's functionality. This lawmaking could be introduced in the backend past more circuitous ways, or submitted simply as a response in a user-facing form. Likewise known as a SQL injection, this happens when an attacker submits a cord of harmful code to a website through some user input, like a contact form. The website then stores the code on its database. Similarly to an XSS attack, the harmful lawmaking runs on the website to fetch or compromise confidential information stored in the database. A backdoor is a file containing code that lets an attacker bypass the standard WordPress login and access your site at whatever time. Attackers tend to place backdoors among other WordPress source files, making them difficult to find by inexperienced users. Even when removed, attackers can write variants of this backdoor and keep using them to bypass your login. Though WordPress restricts what file types users can upload to reduce the run a risk of backdoors, it'south however very much a trouble to be enlightened of. These attacks foreclose authorized users from accessing their own website. DoS attacks are most frequently carried out by overloading a server with traffic and causing a crash. The effects are worsened in the case of a distributed denial-of-service attack (DDoS), a DoS attack conducted past many machines at in one case. When an assailant contacts a target posing as a legitimate company or service, this is known as phishing. Phishing attempts typically prompt the target to give up personal data, download malware, or visit a unsafe website. If an attacker accesses your WordPress business relationship, they could even coordinate phishing attacks on your customers while posing as yous. Hotlinking occurs when another website shows embedded content (usually an image) that is hosted on your website without permission, so that the content appears like it'south their own. While more akin to stealing than a full-diddled attack, hotlinking is normally illegal and gives the victim serious issues, since they have to pay every fourth dimension content is retrieved from their server when displayed on another website. For these crimes to occur, hackers demand to discover holes in a site's security. Common vulnerabilities that hackers wait for when targeting WordPress websites include: For a deeper look at WordPress security issues, see our article on WordPress security bug you should know about. Now that we're past the scary office, let's talk over what you can practice to reduce the threat of a cyberattack on your WordPress website. Website security, and by extension WordPress website security, comes down to following a fix of best practices. Some of these apply to all websites in general (e.thousand. strong passwords and two-gene hallmark, SSL, and firewalls), while others apply specifically to WordPress websites (eastward.g. using secure plugins and a secure WordPress theme). To go on your site at its safest, we recommend adhering to as many of these all-time practices equally yous reasonably tin. First, we'll comprehend the basic best practices. Then we'll add additional steps you can have if your site is especially at take a chance or if yous want to go even further. The well-nigh fundamental step to securing your website is keeping your accounts safe from malicious login attempts. To do this: When choosing the service that hosts your website, there are many factors to take into account, but security should exist a meridian priority. Consider services that have taken steps to protect your information and promptly recover if an assault occurs. Encounter our list of recommended WordPress hosting providers. Outdated versions of the WordPress software are a very common target for hackers. Make certain you regularly check for and install WordPress updates as soon as possible to eliminate vulnerabilities found in older versions. To update WordPress to the latest version, first support your site and check that your plugins are compatible with the latest version of WordPress, updating plugins accordingly. You can reference our guide for how to update your WordPress plugins. After updating your plugins, follow the update instructions on WordPress' website. Upgrading to the latest version of PHP is one of the nearly of import steps you tin take to keep your WordPress website secure. When an upgrade is gear up, WordPress will notify yous on your dashboard. It volition then prompt yous to head to your hosting account to upgrade to the latest PHP version. If you lot don't have access to your hosting account, get in touch with your web developer to upgrade. Nosotros highly recommend installing one or more reputable security plugins on your website. These plugins do much of the security-related manual piece of work for you, including scanning your website for infiltration attempts, altering source files that might go out your site susceptible, resetting and restoring the WordPress site, and preventing content theft similar hotlinking. Some reputable plugins encompass almost everything on this list. This step is not needed if you lot are using HubSpot's Content Management System which provides malware scanning and threat detection within the platform. Whichever plugin(s) y'all make up one's mind to install, security-related or not, brand sure they're well-established and legitimate. Come across our list of recommended WordPress security plugins. Just like you shouldn't install a sketchy plugin on your site, resist the urge to utilize just whatsoever WordPress theme that looks good. To forestall vulnerabilities caused by a WordPress theme, cull one that is compliant with WordPress standards. To check whether your current theme meets WordPress' requirements, copy your website URL (or the URL of any WordPress site or any theme'southward live demo) into W3C's validator. If you find your theme isn't compliant, search for a new theme in the official WordPress theme directory. All themes in this directory are safely compatible with WordPress software. Alternatively, see HubSpot's list of recommended WordPress themes, or search some other credible theme marketplace. SSL (Secure Sockets Layer) is the engineering that encrypts connections between your website and visitors' spider web browsers, ensuring that the traffic between your site and your visitors' computers is prophylactic from unwelcome interceptions. Your WordPress site needs SSL enabled. If y'all're a CMS Hub user, SSL is costless and built into the platform so you're practiced to become. If y'all are using WordPress, then depending on your use case, you may opt to do this manually or use a defended SSL plugin. Not merely will it boost SEO, but information technology also plays directly into your visitors' first impression of your website. Google Chrome will even warn users if the site they're visiting doesn't follow the SSL protocol, which directly reduces website traffic. To see whether your WordPress site follows the SSL protocol, visit your WordPress site'southward homepage. If the homepage URL begins with "https://" (the "s" stands for "secure"), your connection is secured with SSL. If the URL begins with "http://", yous'll need to obtain an SSL document for your website. A firewall sits between the network that hosts your WordPress site and all other networks, and automatically prevents unauthorized traffic from entering your network or organization from the outside. Firewalls keep out malicious activity out of your site past eliminating a direct connectedness betwixt your network and other networks. We recommend installing a Web Application Firewall (WAF) plugin to protect your WordPress site. With the CMS Hub, your site will come with WAF inside the platform. Every bit with everything else on this listing, carefully deliberate which type of firewall and which plugin works best for your needs before making your pick. Being hacked is bad. Losing all your information is even worse. Make sure you have your website information backed up by WordPress and your host in the event of an attack (or whatever other incident) that causes data loss. We recommend backups be automatic every bit well. See our list of the all-time WordPress fill-in plugins available. It's a good idea to run routine check-ups on your site. Aim for at least once a calendar month. There are multiple plugins that tin can scan your site for yous. Here are the seven WordPress scanner plugins we recommend. Once you've taken these basic steps, you can so motion to more than advanced measures to secure your WordPress website. If any role of your website accepts a response from visitors, be information technology a payment form, a contact course, or fifty-fifty a comment section on a blog post, this is an opportunity for an XSS or database injection attack. Attackers could enter malicious lawmaking into whatsoever of these text fields and disrupt your website'due south backend. To avoid this trouble, make sure you filter out special characters from user input earlier it is processed by your site and stored in a database. Y'all can besides utilise a plugin to find malicious code. Alternatively, you tin can employ a WordPress grade plugin to automatically filter out these characters. If your WordPress site has multiple user accounts, nosotros recommend irresolute the roles of each user to limit their access to simply what they need. WordPress has six roles to choose for each user. By limiting the number of users with ambassador permissions, you reduce the chance of an assailant brute-forcing their way into an admin account, and limit the damage that can be done if an attacker does correctly guess a user's credentials. See our guide on how to change WordPress user permissions. Having a monitoring system in identify for your website will alarm you of any suspicious activity that occurs on your site. Ideally, your other measures would take prevented such activeness, simply it'due south better to find out sooner rather than later. You lot tin utilise a WordPress monitoring plugin to get an alert in case at that place'due south a breach. Here's some other mode to go out ahead of issues before they occur: Create a log of all activeness that users accept on your website, and check this log periodically for suspicious activity. This way, you'll see if some other user is acting suspiciously (east.g. trying to alter passwords, altering theme or plugin files, installing or deactivating plugins without permission). Logs are too useful for cleanup later on a hack, showing you what went wrong and when. This isn't to say that all countersign changes or file modifications are always signs of a hacker among your squad. Still, if you lot're employing many external contributors and giving them admission permissions, it'southward always a good thought to keep an eye on things. Many WordPress plugins create action logs, and there are several dedicated logging plugins for WordPress like WP Activeness Log or the free Activity Log plugin. As I've mentioned, the default URL for the WordPress login page for any WordPress site is easy to detect. Plugins like WPS Hide Login change this login page URL for you. By default, WordPress lets administrators edit the code of their files directly with the code editor. This gives attackers an easy manner to alter your files if they gain access to your account. If a plugin hasn't already disabled this characteristic, you can practise some light coding to disable information technology yourself. Add the code beneath to the cease of the file wp-config.php: // Disallow file edits ascertain( 'DISALLOW_FILE_EDIT', true ); The names of the files that brand upwardly your WordPress database begin with "wp_" past default. Hackers leverage this setting to locate your database files by name and carry SQL injections. A simple ready? Change the prefix to something different, like "wpdb_" or "wptable_". It is possible to set up this when installing the WordPress CMS. If your site is already live with this setting, you tin can rename these files. In this case, we highly recommend using a plugin to handle this process, since your database stores all your content and a misconfiguration volition break your website. Wait for the ability to change table prefixes among the features of your preferred security plugin. XML-RPC is a communication protocol that enables the WordPress CMS to interact with external web and mobile applications. Since the incorporation of the WordPress REST API, the XML-RPC is used much less often than information technology once was. However, it is still utilized past some to launch powerful attacks on WordPress sites. This is because XML-RPC applied science lets attackers submit requests containing hundreds of commands, making it easier to commit brute force login attacks. XML-RPC is also less secure than Residue because its requests contain hallmark credentials that tin be exploited. If you're not using XML-RPC, you lot can disable the xmlrpc.php file. Beginning, check whether your site is making use of the file. Plug your URL into this XML-RPC validator to cheque whether your site is currently making use of the protocol. If non, the easiest way to disable this file is with a plugin similar Disable XML-RPC-API. Your WordPress security plugin may likewise exist able to exercise this for you. We've discussed changing the "admin" username for the default WordPress admin business relationship, but if you want to have things a stride further, get rid of this default account altogether, and brand a new account with the same ambassador permissions. This is a good step to take if y'all recollect that your original admin username and password have been discovered. Hiding your WordPress version volition ensure hackers don't know that your site is vulnerable. As covered previously, you must always update to the latest version of WordPress. Only if you haven't notwithstanding gotten the opportunity to do so, it's critical to hide the potential vulnerability. Hither's a tutorial on how to hibernate your WordPress version. Then, you've implemented some or all of the measures above, and now y'all want to be extra prepared in case something goes wrong. Or, something has gone wrong. Either fashion, here's what to do: It's natural to panic in these situations. Merely recollect that a security breach can happen to anyone. Information technology's necessary to go on a clear caput and so you can locate the source of the breach and begin to resolve it. Limiting access to your site keeps visitors away from your side and safe from the assail. Simply open up your website when you lot're confident the state of affairs is under control. Record all relevant details that tin can help solve the outcome. These include, but are not express to: Update this document as more details become available. Change all account passwords on your WordPress site to forestall whatsoever further website changes. Next, force-logout any users still logged in. All business relationship holders should also strongly consider updating passwords on their work and personal devices, as well equally personal accounts, since you tin't know for sure what the attackers were able to access beyond your WordPress site. Either search for the problem yourself with a security plugin, or, depending on the calibration of the attack, rent a professional to diagnose the problem and repair your site. Regardless of what method yous choose, run a security scan on your site and local files to clear whatsoever remaining harmful files or lawmaking the attackers might accept left, and to restore any missing files. If you have accounts for any other online platform linked to your website, such as a social media business relationship or another WordPress site, cheque these platforms to come across if they were affected. Change your passwords for these channels also. Re-install your theme and plugins (double-checking that they're condom). If you have a backup in place, restore the most recent backup prior to the incident. Yes, you did reset all WordPress passwords before, but these credentials could have been compromised while you lot were fixing the problem. You can never be also careful. After your site is up and running again, strongly consider reaching out to your customers alerting them of the attack, especially if personal information was accessed and leaked. It's the right thing to do, and exist prepared for negative responses from customers. If your website was blacklisted by Google as a result of the set on, Google will not-so-subtly warn users about inbound your website: While blacklisting is necessary to go on users away from harmful websites, information technology will likewise scare most traffic from your legitimate site. Sucuri has a free tool to scan your website for Google blacklist condition. Taking all possible precautions to limit the possibility of another set on will give you some peace of mind. Let's hope something similar this doesn't happen over again. But if information technology does, yous'll be in much improve shape. Cybercriminals are constantly evolving new ways to leverage companies' online presence against them, and security engineers are always developing new methods to stop them. This is the always-turning cycle of security on the internet, and nosotros're all caught in the eye. E'er keep your customers' condom in mind, and so they have one less thing to worry most. Note: Any legal information in this content is not the same as legal advice, where an attorney applies the constabulary to your specific circumstances, so we insist that you lot consult an chaser if you'd like advice on your interpretation of this information or its accuracy. In a nutshell, you may not rely on this as legal advice or as a recommendation of whatever particular legal understanding. Editor's annotation: This post was originally published in May 2020 and has been updated for comprehensiveness. Why You Demand WordPress Security
It protects your information and reputation.
Your visitors expect it.
Google likes secure websites.
How safe is WordPress?
WordPress Security Bug
Brute-Force Login Attempts
Cantankerous-Site Scripting (XSS)
Database Injections
Backdoors
Denial-of-Service (DoS) Attacks
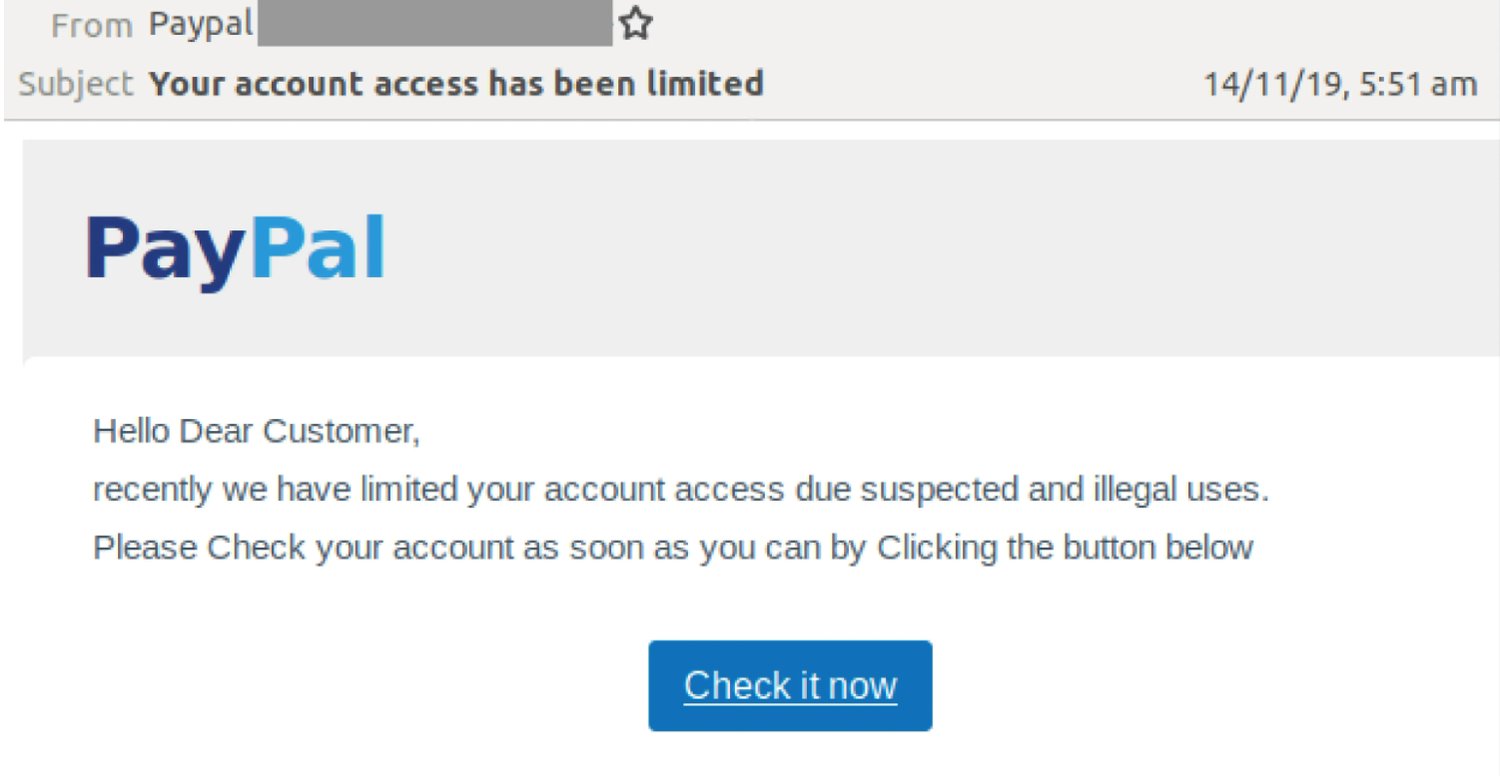
Phishing
Hotlinking
How to Secure Your WordPress Site
WordPress Security Best Practices
1. Secure your login procedures.
2. Use secure WordPress hosting.
iii. Update your version of WordPress.
four. Update to the latest version of PHP.
v. Install one or more security plugins.
half-dozen. Utilise a secure WordPress theme.
seven. Enable SSL/HTTPS.
eight. Install a firewall.
ix. Back up your website.
ten. Conduct regular WordPress security scans.
Advanced WordPress Security Best Practices
one. Filter out special characters from user input.
two. Limit WordPress user permissions.
3. Use WordPress monitoring.
4. Log user activity.
5. Modify the default WordPress login URL.
6. Disable file editing in the WordPress dashboard.
7. Modify your database file prefix.
eight. Disable your xmlrpc.php file.
9. Consider deleting the default WordPress admin account.
10. Consider hiding your WordPress version.
What To Do If You're Hacked
1. Remain calm.
2. Turn on maintenance mode on your website.
3. Outset creating an incident report.
4. Reset access and permissions.
v. Diagnose the consequence.
6. Review related websites and channels.
vii. Reinstall fill-in, themes and plugins.
eight. Change your site passwords again.
ix. Alert your customers and stakeholders.
10. Check that your website is not blacklisted by Google.
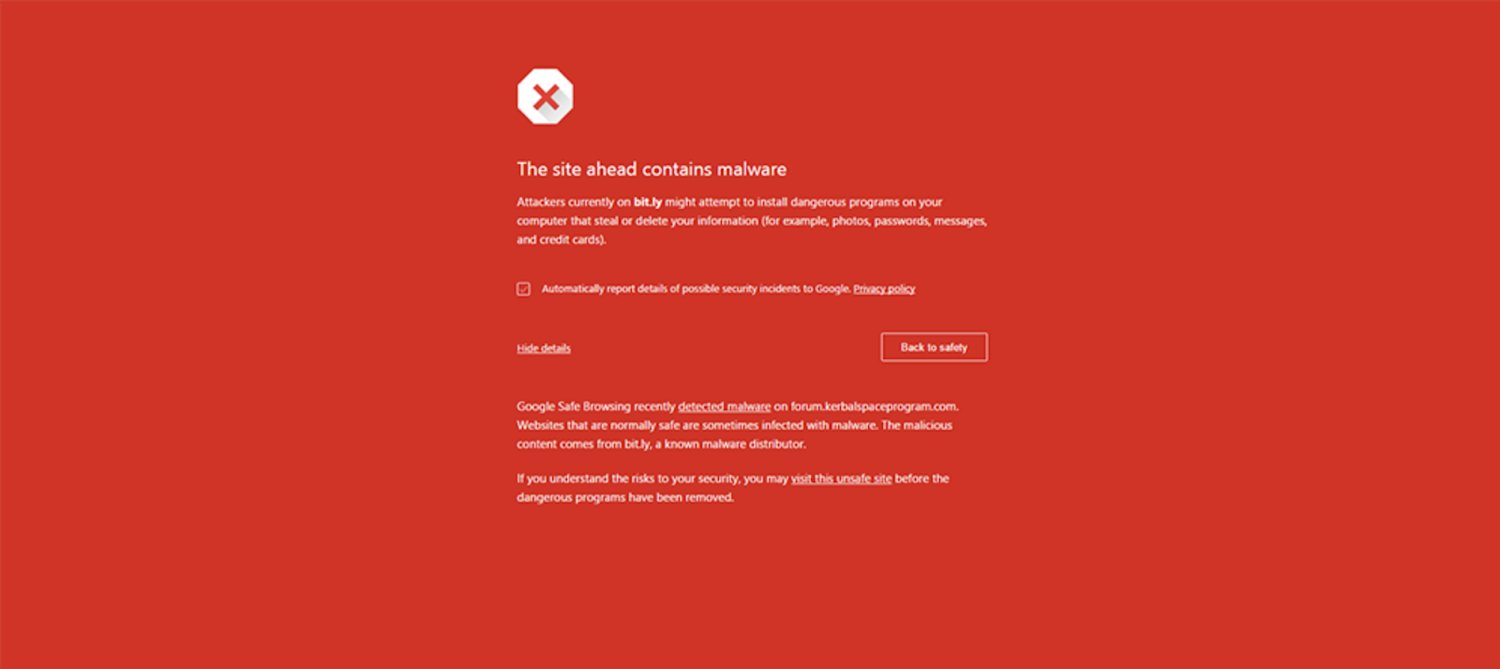
xi. Follow the best practices in a higher place.
Don't accept security for granted.
Originally published Nov 18, 2021 7:00:00 AM, updated March 25 2022
How to Make Secure Website in Wordpress
Posted by: leopardthimemper.blogspot.com